Security operations center (SOC) solutions help strengthen an organization’s cybersecurity posture by monitoring all its devices, services, networks, and servers, investigating incidents, resolving security issues, and protecting it from attacks.
Organizations worldwide are concerned about their cybersecurity since attackers are targeting everyone, which can compromise data and cause monetary and reputational losses.
Thus, you need to stay one step ahead of attackers by adopting advanced ways like SOC to stay protected.
In this article, I’ll introduce you to the realm of SOC, its benefits, and some of the best SOC solutions you can consider using.
Best Security Operations Center Solutions
Let’s now discuss some of the best SOC tools for your organization.
Microsoft Sentinel
Use Microsoft Sentinel, which leverages the power of AI and cloud computing to modernize and simplify your organization’s security operations center (SOC). This tool will help you find advanced threats quickly and respond to them proactively with a comprehensive, intelligent security information and event management (SIEM) solution.

Key Features
- Data collection: Collects data at scale from all devices, infrastructures, users, and applications in different clouds and on-premises
- Detection: The tool can detect threats that were not found previously and reduce false positives through Microsoft’s threat intelligence and data analytics
- Investigation: Using AI and Microsoft’s cybersecurity efforts carried out over the years, Sentinel can investigate security threats and suspicious activities at scale.
- Response: Sentinel can respond to security incidents quickly with its built-in capabilities and task automation.
- Other features: Correlated event analysis, viewing alert lists on priority, understanding attack scopes, threat behavior analysis,
One of the great things about this cloud-native SIEM solution I noticed is that it does not restrict users with query or storage limits, giving you the freedom and power to protect your organization.
Try it free and get 200 credits for 30 days or create your account with a pay-as-you-go plan.
Try Microsoft Sentinel
ManageEngine Log360
Log360 by ManageEngine is an integrated SIEM solution with CASB and DLP capabilities to detect, investigate, prioritize, and respond to threats. For detecting advanced threats, this tool uses techniques like ML-based anomaly detection, rule-based attack detection, and threat intelligence.

Its incident management console helped me eliminate all the detected threats effectively. I really like its sophisticated and intuitive security monitoring and analytics capabilities that provide enhanced visibility across cloud, on-preemies, and hybrid networks.
Key Features
- Log management: You can gather logs from multiple sources like servers, end-user devices, network devices, antivirus software, firewalls, etc.
- Easy to understand dashboard: Log360’s dashboards make it easier to analyze logs with data represented as graphs and reports. It helps in detecting attacks and anomalies and preventing them.
- Active Directory (AD) changes: Monitor and track AD changes and suspicious behavior to better mitigate threats.
- Cloud Security: Get better visibility into cloud infrastructures like GCP, Salesforce, Azure, AWS, etc. Monitor changes in your network security, users, VPCs, etc., in real-time.
- Time management: Aggregate security information from multiple platforms like Microsoft 365, Exchange Server, SaaS, PaaS, IaaS, servers, apps, network devices, etc., into one console and automate responses to accelerate threat resolution.
- Threat hunting: Use an event response system to perform log searching and get alerted in real-time about threats and stop them.
- Compliance management: Comply with regulatory bodies like HIPAA, GLBA, PCI DSS, FISMA, SOX, ISO, and more by producing audit-ready reports that you can create using templates and stay vigilant through compliance violation alerts.
Try ManageEngine Log360, free for 30 days.
Try ManageEngine Log360
Heimdal
Heimdal offers a single but powerful platform to perform threat hunting, manage data and alerts, and respond to incidents in real-time with full context at all levels. It offers network and endpoint security, privileged access management, vulnerability management, unified endpoint management, and email and collaboration security.

I’m amazed at the Threat-hunting & Action Center by Heimdal, which derives its power from its sophisticated XTP engine along with the Heimdal suite.
Key Features
- Unified interface: Heimdal provides a unified and clear interface that not only lets you view threats but also manage them and take action.
- SecOps Toolkit: The tool comes with a power-packed SecOps toolkit in a single place with capabilities like thorough visualizations, risk scores, attack analysis, indicators, threat hunting, and remediation.
- MITRE ATT&CK framework and XTP Engine: These technologies power teams to infinitely detect and monitor anomalies at the endpoint level, generate risk scores, and perform forensic analysis.
Heimdal’s Action Center will help you make quick but correct decisions on the go by running and executing commands like threat scanning, isolation, and quarantine.
Try Heimdal
Xcitium Complete MDR
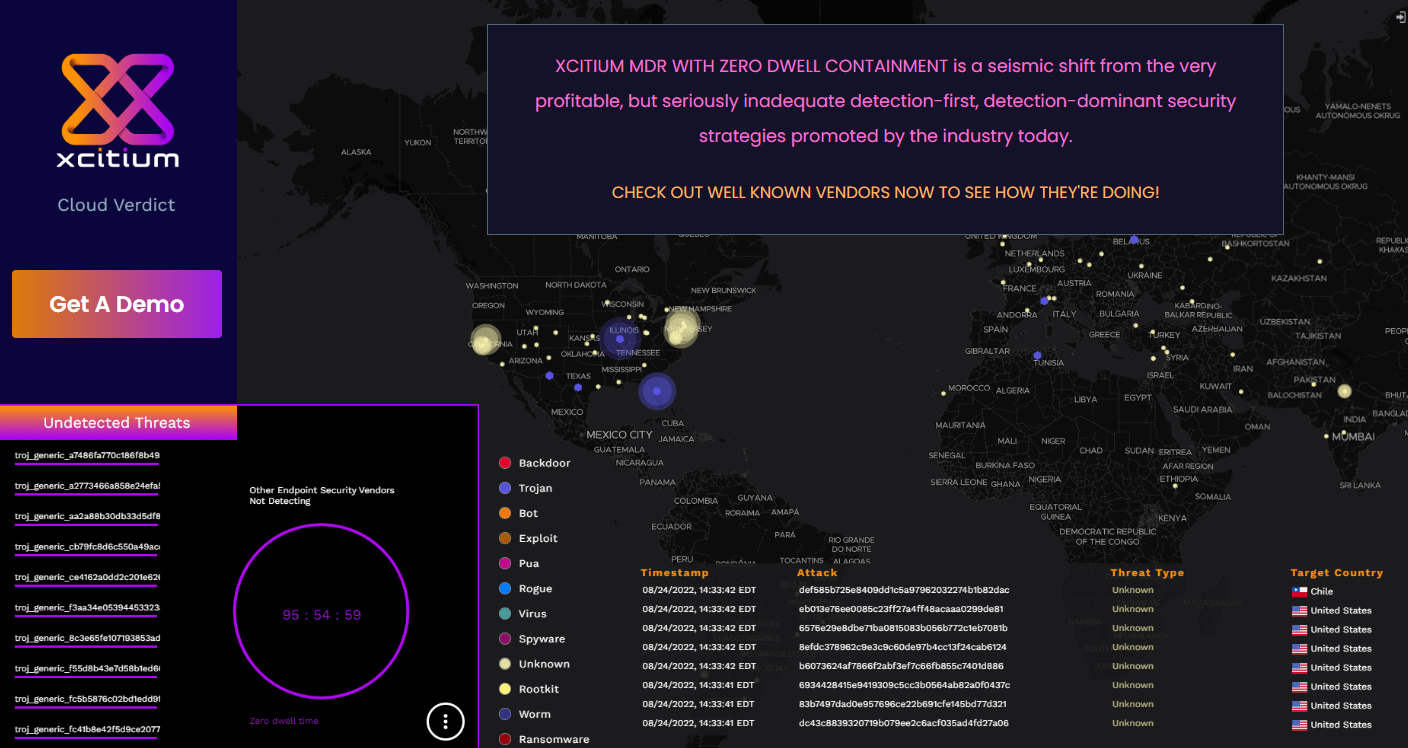
Enhance your cybersecurity with Xcitium Complete MDR that provides full-context visibility, risk-based and targeted threat hunting, and continuous response and monitoring. Here, MDR means managed detection and response.
Key Features
- Full-service MDR: Xcitium provides expert-level management, ZeroDwell Containment, free incidence response, forensics, and hardening of security profiles.
- Reduced complexity: With 24/7/365 continuous security monitoring, short MTTR, and fast SLAs, I found Xcitium to be one of the fastest, most cost-conscious, and most efficient MDR service providers.
- Faster time-to-value: Xcitium offers many built-in integrations, deeper visibility, automated virtualization, and real-time context, with smooth operations without alert fatigue.
- Other features: Forensic analysis, expert administration, identity protection, SOC analysis, real-time automated AI and ML-based correlations and context, and more.
So, instead of fearing unknown threats, use Xcitium Complete MDR to contain threats.
Try Xcitium Complete MDR
Apex Central
Improve your organization’s security posture and reduce IT burdens using Apex Central’s centralized threat investigation and visibility capabilities. It can bridge the SOC and IT silos that can separate different layers of deployment and protection models.
One interesting thing that I noticed is that users can view threat activity patterns across organization groups and devices with visual timelines, which helps remove security vulnerabilities.
Key Features
- Centralized security: You can monitor and learn the security posture of your company, detect threats, and address them faster. It will help you ensure consistent threat protection data and policies are implemented across your networks, servers, web, emails, and endpoints on both on-premises and cloud.
- Dashboard: Visualize your security operations in a clear dashboard that can integrate easily with your Active Directory, providing timeline-based and user-based security incident views.
- Unified console: Using its unified console, it will become easier for you to investigate alerts and prioritize them for resolution.
- Robust reporting: Understand threats and compliance issues using intuitive reports with heat maps. Apex Central also offers custom, standard, and simple reporting options.
- XDR: With comprehensive extended detection and response (XDR), you can collect data and automatically correlate it across different security layers like servers, emails, endpoints, etc.
Get started with Apex Central now.
Try Apex Central
LogRhythm
LogRhythm is a self-hosted SIEM platform that can help you quickly detect and resolve security incidents while reducing associated expenses. It provides dashboards, embedded modules, and rules so you can achieve your SOC goals.

When I used LogRhythm, I found that its incident response technique is seamless, while its analytics is intuitive and high-performing.
Key Features
- Complete visibility: LogRhythm offers complete visibility of your security posture from your networks and endpoints to servers and cloud services. You can also perform log searching to detect security issues.
- Visual analyst: Working like a visual analyst, the tool helps security teams prioritize tasks by analyzing security posture and available data.
- Automation and collaboration: The tool can automate tasks and collaborate on threat investigations so you can remediate issues faster.
- Scalable and easy: Using LogRhythm is easy, even if your security requirements are lower or higher. The tool can quickly scale with your growing needs, supplying performance and reducing costs.
- Other features: LogRhythm offers centralized log collection and management, MDI to enrich and contextualize data and translate complex info into actionable insights, alerts, event timelines, reports, SOAR (security orchestration, automation, and response) capabilities, and more.
Schedule a demo now.
Try LogRhythm
Exabeam
Use Exabeam to simplify your security operations and accelerate them to get better protection. It is one of the most advanced and cloud-based security operations tools to perform threat investigation, detection, and response. Also, it leverages emerging technologies like AI to secure networks, devices, servers, clouds, etc.

Key Features
- SEIM and Log management: Using Exabeam, it was pretty easy to ingest, store, and parse data securely. I’m also amazed at its lightning-fast search capabilities, dashboards, reporting, threat intelligence, powerful correlation, etc.
- Behavioral analytics: ML-based behavioral analytics helps enhance detection capabilities and automate timelines to prioritize anomalies according to risks.
- Data enrichment: Exabeam can enrich your data in three ways – user-host IP mapping, geolocation, and threat intelligence. This way, it helps prioritize risks and improve detection accuracy.
- Extensibility: Exabeams data collection spread over 200 on-premises products, over 20 cloud infrastructure products, over 10 SaaS apps, and 34 cloud-based security products. It supports agents, APIs, log aggregators, and syslogs.
- Compliance: You will get compliance reports for SOX, PCI DSS, and GDPR.
Apart from that, Exabeam has 10k+ pre-built parsers, 2M+ events per second, and 2500+ models and rules.
Try Exabeam
InsightIDR
InsightIDR by Rapid7 offers a unified XDR and SIEM tool that’s cloud-native and lightweight. It will monitor your complete attack surface using automated response and embedded threat intelligence with less noise.

The tool can anticipate threat behavior by baselining activities that are considered healthier and using its sophisticated detection library.
Key Features
- You can also analyze data quickly and scale efficiently using the tool with detailed timelines and playbooks.
- It helps integrate the tool with your cloud solutions seamlessly
- It automates incident investigation and management
- Displays all data clearly in its dashboard for effective analysis and remediation
- Trustworthy detections with no alert fatigue
- Network traffic analysis and SIEM
- User and entity behavior analytics (UEBA)
Get started with InsightIDR now.
Try InsightIDR
NeoSOC
NeoSOC is a cloud-based, 24/7 managed security service. I noticed that it comes with a SOC-as-a-service deployment model, which offers greater flexibility for users.

The best thing is that You will get fully managed threat detection and response tailored to your needs. This is a scalable solution suitable for organizations of different sizes.
Key Features
- Device monitoring 24/7
- Alerting
- Supports 400+ applications and devices as log sources for clear visibility
- Its VM log collector is quick to deploy
- Cross-customer and cross-device correlation and analysis
- SIEM with ML for accurate detection and lower false positives
- Advanced persistent threat detection via custom use cases
Take a free trial to know more.
Try NeoSOC
Swimlane
Swimlane provides AI-powered automation to secure your entire organization from attacks. It allows you to build low-code automation tasks and apply them with cloud, SecOps, audit, compliance, and other areas.

The tool will help you keep up with emerging threats, alerts, and complicated security processes in order to secure your company.
Key Features
- Telemetry ingestion from hard-to-reach data sources to lower dwell time and accelerate MTTR
- Easy to integrate with multiple security systems without heavy coding
- Streamlined playbook building to enable automation
- Unifies teams, telemetry, and workflows
Try Swimlane
Let’s now explore the concept of a Security Operations Center (SOC), delve into the advantages of employing SOC tools, and learn how to select the most suitable SOC tool.
What Do You Mean by a Security Operations Center?
A Security Operations Center (SOC) is like a central hub of an organization comprising expert security professionals who are responsible for keeping an eye on the organization’s security and protecting it from attacks.

The main elements of a SOC are:
- People: These are the security professionals who constantly monitor every device, network, data, server, cloud services, and other endpoints used throughout the organization so that no vulnerability remains in them and keeps them protected.
- Processes: SOC professionals adopt some techniques and processes to safeguard the organization’s security. These processes could be continuous monitoring, accounting, and assessing all endpoints and their security, performing regular maintenance, updating devices and applications, responding to threats, performing recovery, and more.
- Technology: A SOC team can perform different security processes either manually or using tools. For example, they use antivirus applications to detect viruses. You can also use SOC tools to get comprehensive security that can take care of everything from monitoring and detection to resolution and investigation.
Overall, SOC can unify your organization’s security practices, tools, and threat response. As a result, your security efforts will be enhanced.
Benefits of Using Security Operations Center Tools
Using security operations center (SOC) tools in your organization will streamline your entire cybersecurity efforts. Here’s how.
Faster Threat Detection
SOC tools allow you to find and monitor all your internet-connected devices, servers, networks, applications, and services that are on-premises and in the cloud.

Thus, you will be able to detect security threats quickly as soon as they appear and neutralize the threats on time before they can infiltrate your organization.
Reliable Remediation
With a SOC tool, you can understand the root cause of a security issue. This will help you remediate the issues effectively based on the context and severity of the attack.
This way, you can protect your devices and systems while also ensuring no traces are left to make your systems vulnerable to attacks again.
Automation
Modern SOC tools come with advanced capabilities like AI and ML to provide several benefits like accuracy, automation, prediction, etc. For example, you can automate many routine tasks like scheduling scans, generating periodic reports, monitoring, etc.
In addition, many SOC tools come with predictive intelligence to forecast the likelihood of attacks associated with a vulnerability and how much damage they can do to your organization. That way, you can eliminate the risks quickly and stay safe.
Efficiency
When you enhance your organization’s security using a SOC tool, you are likely to save huge costs that could otherwise be wasted on repairs and maintenance after an attack. So, investing in a SOC tool is actually cost-efficient.
This also helps you enhance your reputation in the market and among your customers that they are dealing with a safe organization. In addition, you can stay compliant with regulatory bodies and avoid penalties.
How to Choose the Best SOC Tool?
You will find plenty of SOC tools in the market, each with attractive features and capabilities. So, when choosing the best SOC tool for your organization, keep in mind a few things:
- Assess your organization’s security requirements. Take into consideration your organization’s size and number of devices, systems, applications, etc. used in your network. Choose a SOC tool that provides enough coverage.
- Check if the SOC tool you are choosing is scalable in the future based on your needs.
- Choose a SOC tool that has advanced features that can address growing threats.
- Look for a tool whose pricing is suitable for your budget. Compare the features and pricing of different SOC tools and find the best pick.
Wrapping Up
Using the best security operations center solutions like the above, it will become easier for you to streamline your cybersecurity efforts and better protect your organization from attacks. SOC tools will not only help you monitor and detect threats but also resolve them and investigate the full case.
So, go ahead and choose the best SOC tool based on your organization’s security requirements and budget.



